XVerginia V4 Phishing Kit Created by ShadowZ118
Phishing Kit posted to Virus Total 4/27/2020
https://www.virustotal.com/gui/file/e152510758a727e16986a6c8ba55b51b572d0087ec2afb475f7ada29b72317e7/relations
md5 67529f8a7bdce0119589c15d44c3d131
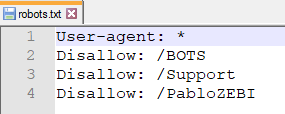
At it's root folder there is a robots.txt : used to restrict which search engines index it
The .htaccess file also prevents certain sources, user agents, etc. from accessing the site all likely in an attempt to prevent security researchers and search engines from crawling, indexing, or finding the phishing site.
The index.php if the default page that anybody will receive when landing in this directory on the website, as long as they haven't been blocked by the .htaccess or the robots.txt files for example. In this case index.php contains the supposed name of the phishing kit and version number "XVERGINIA V4". Then it starts in again with more attempts to block security researchers and crawlers from indexing or finding the website
The index.php otherwise is small and only has a few lines of code. It has the author of the phishing kit "ShadowZ118" which is actually the name of a sub-folder seen above in the 1st screenshot also. This phishing kit differs from a few of the more common phishing kits because this kit chooses to make an entire copy of the phishing kit folder "ShadowZ118" for every single USER! So if this threat actor gets a bunch of victims, there will be a bunch of sub-folders in their web directory and then at the end of this folder creation it redirects the victim to their new unique sub folder that is just created using the Location header.
Above in index.php you noticed a bunch of blocker and antibots php files that get included. This is yet again just another fall back attempt to block as many security researchers, security tools, and search engines as possible by ip address, keyword, etc. and direct them to a 404 page. That means if you're coming from one of those companies, or you try to load this site in one of those tools, such as phish tank, the page will return a 404 instead of actually loading the credential phishing page. It's intended to trick a security researcher into thinking the site was already taken down which it actually wasn't yet.
The ShadowZ118 as said above is the main credential phishing page where a fake Paypal page is going to be presented and passwords stolen. This is not the folder the victim would go to, but it actually gets completely copied into a new random folder first and then the victim is directed to that randomly named copy of the folder. But reviewing the ShadowZ118 folder will give you the most details about what this phish is after. The victim will start at the index.php file as that is the default for a web server. As you can see below this loads 3 php files before making a decision with the if statement. The 1st php file, xanbbx.php is just another anti-security researcher file with lists of ip addresses to ban and redirect to a 404 page, so nothing exciting. The 2nd php page "Config.php" arguably the most valuable file in the whole phishing kit. It is where the script kiddie that purchased the phishing kit gets to fill in his email address (where stolen passwords will be sent) plus toggle a few configurations such as enabling captcha , setting an administrative password for the phishing panel , and toggling whether or not to save the stolen passwords directly into a file on the web server. In this case the script kiddie's email is a gmail account (nerogammer77[@]gmail[.]com) , their admin password is 'a' , they are not using a captcha, and yes they are saving all the victim passwords directly to a file on the web server, thus victims could easily be identified if a security incident response team did forensics on the web server.
In addition if you recall at the top of index.php was an include to a cookies.php. This file is actually very dangerous as it will try to take advantage of any victim that is already signed into Paypal prior to visiting the phishing site. If the victim was already signed into Paypal prior to visiting the site, the attacker forces the user's browser to visit the official paypal.com website and steals the victims credit card number, bank account numbers, and street address. Finally if you recall back on index.php after all the included php files are loaded, it makes a deciion .. if captcha was enabled in the config.php file then the victim would get redirected to a captcha page, otherwise they'd get sent to the standard credential phishing page (indexx.php) notice 2 letter x's in the name.
The indexx.php page includes several additional php pages that load before it redirects you to the "myaccount\sign-in" sub folder and passes the country code / language that it will present the phish to the victim in.
The get_ip.php file makes a call to the ip-api.com api which tells the threat actor what ip address the victim is coming from so it can be logged.
The xanbbx.php is the anti security researcher page again and the config.php is the configuration file, both of those files will be included on every other page likely. The 4th page is the get_lg.php which uses the get_ip.php page above to determine the language to present the page in (English, Spanish, Chinese, etc.). This is needed before the redirect mentioned above to the my account sign-in page so the threat actor knows what language to display it in.
The XYSRNX.php just generates 2 variables, 1 with the victim's user agent string, and one with the current date/time and then the indexx.php page sends the victim to the myaccount/sign-in page. Notice there are 2 Sign-in pages/folders because there is a new and older version and the phishing kit creator supports backwards compatibility of both versions. The index.php page in the myaccount\Sign-in folder (screenshot below) includes all the anti-security researcher pages again, some files that configure the language, and it contains the actual credential phishing textboxes and buttons (such as username and password) even though some of it is javascript encoded.
In the index.php page above you notice that the form submit takes you to XSEND_LOGINX.php so that is the page we want to review next. This is where the stolen password is sent to be processed. You'll notice that the username and password were sent from the previous page via session variables. If you look closely below in the $xysmsgx variable you'll see an email body that includes data like the victim's ip address, user agent, username, password, etc You'll also see extra variables for the email's subject like, from line, content type. And finally you'll see the call to the php mail function which will send the email to the email address in the "Config.php" file. Notice it will also write the entire email including stolen password to a a file called "/ShadowZ118/myaccount/identity/INC/ID.html" so this is a quick spot to find a list of all the victims.
https://www.virustotal.com/gui/file/e152510758a727e16986a6c8ba55b51b572d0087ec2afb475f7ada29b72317e7/relations
md5 67529f8a7bdce0119589c15d44c3d131
At it's root folder there is a robots.txt : used to restrict which search engines index it
The .htaccess file also prevents certain sources, user agents, etc. from accessing the site all likely in an attempt to prevent security researchers and search engines from crawling, indexing, or finding the phishing site.
The index.php if the default page that anybody will receive when landing in this directory on the website, as long as they haven't been blocked by the .htaccess or the robots.txt files for example. In this case index.php contains the supposed name of the phishing kit and version number "XVERGINIA V4". Then it starts in again with more attempts to block security researchers and crawlers from indexing or finding the website
The index.php otherwise is small and only has a few lines of code. It has the author of the phishing kit "ShadowZ118" which is actually the name of a sub-folder seen above in the 1st screenshot also. This phishing kit differs from a few of the more common phishing kits because this kit chooses to make an entire copy of the phishing kit folder "ShadowZ118" for every single USER! So if this threat actor gets a bunch of victims, there will be a bunch of sub-folders in their web directory and then at the end of this folder creation it redirects the victim to their new unique sub folder that is just created using the Location header.
Above in index.php you noticed a bunch of blocker and antibots php files that get included. This is yet again just another fall back attempt to block as many security researchers, security tools, and search engines as possible by ip address, keyword, etc. and direct them to a 404 page. That means if you're coming from one of those companies, or you try to load this site in one of those tools, such as phish tank, the page will return a 404 instead of actually loading the credential phishing page. It's intended to trick a security researcher into thinking the site was already taken down which it actually wasn't yet.
The ShadowZ118 as said above is the main credential phishing page where a fake Paypal page is going to be presented and passwords stolen. This is not the folder the victim would go to, but it actually gets completely copied into a new random folder first and then the victim is directed to that randomly named copy of the folder. But reviewing the ShadowZ118 folder will give you the most details about what this phish is after. The victim will start at the index.php file as that is the default for a web server. As you can see below this loads 3 php files before making a decision with the if statement. The 1st php file, xanbbx.php is just another anti-security researcher file with lists of ip addresses to ban and redirect to a 404 page, so nothing exciting. The 2nd php page "Config.php" arguably the most valuable file in the whole phishing kit. It is where the script kiddie that purchased the phishing kit gets to fill in his email address (where stolen passwords will be sent) plus toggle a few configurations such as enabling captcha , setting an administrative password for the phishing panel , and toggling whether or not to save the stolen passwords directly into a file on the web server. In this case the script kiddie's email is a gmail account (nerogammer77[@]gmail[.]com) , their admin password is 'a' , they are not using a captcha, and yes they are saving all the victim passwords directly to a file on the web server, thus victims could easily be identified if a security incident response team did forensics on the web server.
In addition if you recall at the top of index.php was an include to a cookies.php. This file is actually very dangerous as it will try to take advantage of any victim that is already signed into Paypal prior to visiting the phishing site. If the victim was already signed into Paypal prior to visiting the site, the attacker forces the user's browser to visit the official paypal.com website and steals the victims credit card number, bank account numbers, and street address. Finally if you recall back on index.php after all the included php files are loaded, it makes a deciion .. if captcha was enabled in the config.php file then the victim would get redirected to a captcha page, otherwise they'd get sent to the standard credential phishing page (indexx.php) notice 2 letter x's in the name.
The indexx.php page includes several additional php pages that load before it redirects you to the "myaccount\sign-in" sub folder and passes the country code / language that it will present the phish to the victim in.
The get_ip.php file makes a call to the ip-api.com api which tells the threat actor what ip address the victim is coming from so it can be logged.
The xanbbx.php is the anti security researcher page again and the config.php is the configuration file, both of those files will be included on every other page likely. The 4th page is the get_lg.php which uses the get_ip.php page above to determine the language to present the page in (English, Spanish, Chinese, etc.). This is needed before the redirect mentioned above to the my account sign-in page so the threat actor knows what language to display it in.
The XYSRNX.php just generates 2 variables, 1 with the victim's user agent string, and one with the current date/time and then the indexx.php page sends the victim to the myaccount/sign-in page. Notice there are 2 Sign-in pages/folders because there is a new and older version and the phishing kit creator supports backwards compatibility of both versions. The index.php page in the myaccount\Sign-in folder (screenshot below) includes all the anti-security researcher pages again, some files that configure the language, and it contains the actual credential phishing textboxes and buttons (such as username and password) even though some of it is javascript encoded.
In the index.php page above you notice that the form submit takes you to XSEND_LOGINX.php so that is the page we want to review next. This is where the stolen password is sent to be processed. You'll notice that the username and password were sent from the previous page via session variables. If you look closely below in the $xysmsgx variable you'll see an email body that includes data like the victim's ip address, user agent, username, password, etc You'll also see extra variables for the email's subject like, from line, content type. And finally you'll see the call to the php mail function which will send the email to the email address in the "Config.php" file. Notice it will also write the entire email including stolen password to a a file called "/ShadowZ118/myaccount/identity/INC/ID.html" so this is a quick spot to find a list of all the victims.




















Comments
Post a Comment