PrinceDuScam - Phishing Kit Type
PrinceDuScam Phishing Kit is just another paypal phishing kit
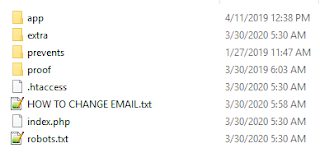
It has some of the standard files like a robots.txt to try to block search engines from indexing the phish, a .htaccess file to also try to block search engines and researchers, an instructional text file for the script kiddie that bought the kid, and an index.php where the fun begins.
The robots.txt blocks access to certain folders so google doesn't index them
The main index.php is the default page that any victim will be dropped to, but it just redirects to another page inside the "app" folder.
The default index page in the "app" folder starts the scam, you can see they include multiple php files that are called "PrinceDuScam" , but these are actually just the common php files used to block security researchers and search engines from crawling and indexing the website and instead returning 404 if the kit detects a researcher or security tool. You can also see that it's going to log victims/visitors in a text file called "log.txt" at the root folder so this could be a forensic starting point for determining the victims during IR. The last snippet of code you can see actually redirects the victim to yet another page called "signin.php"
The signin.php file actually has the textbox for username and password to steal the credentials, but it doesn't send them anywhere yet except to the next page of the scam called step1.php
In the stockers folder you'll see this scam is multi-staged, each stage the attacker will send more stolen details back to their drop account. A victim is thus given multiple opportunities to give away all their personal information including password, street address, bank info, credit card, etc.
In step1.php you see the first reference to the "mine.php" which is actually the file where the script kiddie will place his email address. You can also see in here that the stolen password will get logged to a file called "stored.txt" in the root folder so there is another place to look during an IR if you're doing forensics on who the victims were. You also see at the bottom the tell-tale sign of a phishing kit, as there are 2 php "mail" statements indicating the stolen password is getting sent somewhere, in this case to the "mine.php" email address before going to the next step.
In step2.php you confirm that this scam is definitely also collecting stolen credit cards, not just passwords
Here is the mine.php that contains the email address, in this case younesmouh14[@]gmail[.]com
It has some of the standard files like a robots.txt to try to block search engines from indexing the phish, a .htaccess file to also try to block search engines and researchers, an instructional text file for the script kiddie that bought the kid, and an index.php where the fun begins.
The instructions file tells the script kiddie where to put their drop email account so they can receive the stolen passwords.
The robots.txt blocks access to certain folders so google doesn't index them
The main index.php is the default page that any victim will be dropped to, but it just redirects to another page inside the "app" folder.
The default index page in the "app" folder starts the scam, you can see they include multiple php files that are called "PrinceDuScam" , but these are actually just the common php files used to block security researchers and search engines from crawling and indexing the website and instead returning 404 if the kit detects a researcher or security tool. You can also see that it's going to log victims/visitors in a text file called "log.txt" at the root folder so this could be a forensic starting point for determining the victims during IR. The last snippet of code you can see actually redirects the victim to yet another page called "signin.php"
The signin.php file actually has the textbox for username and password to steal the credentials, but it doesn't send them anywhere yet except to the next page of the scam called step1.php
In the stockers folder you'll see this scam is multi-staged, each stage the attacker will send more stolen details back to their drop account. A victim is thus given multiple opportunities to give away all their personal information including password, street address, bank info, credit card, etc.
In step1.php you see the first reference to the "mine.php" which is actually the file where the script kiddie will place his email address. You can also see in here that the stolen password will get logged to a file called "stored.txt" in the root folder so there is another place to look during an IR if you're doing forensics on who the victims were. You also see at the bottom the tell-tale sign of a phishing kit, as there are 2 php "mail" statements indicating the stolen password is getting sent somewhere, in this case to the "mine.php" email address before going to the next step.
In step2.php you confirm that this scam is definitely also collecting stolen credit cards, not just passwords
Here is the mine.php that contains the email address, in this case younesmouh14[@]gmail[.]com







Comments
Post a Comment