Dropbox Phishing
Live site 5/18/2020
https://urlscan.io/result/a99c116c-3394-4b41-884c-ba62394f4b04
hxxps[:]//www.homehealthot[.]net/wp-includes/docs/content/
phishing kit found at
hxxps[:]//www.homehealthot[.]net/wp-includes/docs/content/dropbox1.zip
threat actor email addresses
Bensonworkman[@]yandex[.]com tanushka1988[@]mail[.]ua md5 e4f157e1cf351227596c3bbd6577514d
https://www.virustotal.com/gui/file/c230927c122c692416a37efbb1938cc0cf9e18a3bdae567ee958e5642191fbb4/details
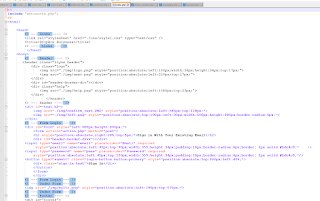
index.php
- references antiboots.php (to block search engines, crawlers, researchers, etc.)
- it has a form that posts stolen credentials to action.php
antiboots.php
- not very exciting, just ip addresses and a few names that redirect to 404 page
action.php
- where we see the guts of the drop account exfil
- including a reference to "to.php" which contains drop email accounts
- and a from reference
$Headers = "From: DROPBOX 2016 <Vip@163.goooo>\r\n";
- routes victim to processing.php
to.php
- contains the threat actor drop email accounts
processing.php
- just a css spinner
- redirects victim to phone_number.php
header( "refresh:3;url=phone_number.php" );
phone_number.php
- collects phone number in a form and posts to action2.php
<form action="action2.php" method="post">
action2.php
- second exfil email sent to same drop account in to.php
- then victim redirected to success.php
header("location: success.php");
success.php
- sends user to a legit pdf
header( "refresh:1;url=http://www.businessmodelcommunity.com/fs/Root/8jig8-businessmodelsbusinessstrategy.pdf" );
https://urlscan.io/result/a99c116c-3394-4b41-884c-ba62394f4b04
hxxps[:]//www.homehealthot[.]net/wp-includes/docs/content/
phishing kit found at
hxxps[:]//www.homehealthot[.]net/wp-includes/docs/content/dropbox1.zip
threat actor email addresses
Bensonworkman[@]yandex[.]com tanushka1988[@]mail[.]ua md5 e4f157e1cf351227596c3bbd6577514d
https://www.virustotal.com/gui/file/c230927c122c692416a37efbb1938cc0cf9e18a3bdae567ee958e5642191fbb4/details
index.php
- references antiboots.php (to block search engines, crawlers, researchers, etc.)
- it has a form that posts stolen credentials to action.php
antiboots.php
- not very exciting, just ip addresses and a few names that redirect to 404 page
action.php
- where we see the guts of the drop account exfil
- including a reference to "to.php" which contains drop email accounts
- and a from reference
$Headers = "From: DROPBOX 2016 <Vip@163.goooo>\r\n";
- routes victim to processing.php
to.php
- contains the threat actor drop email accounts
processing.php
- just a css spinner
- redirects victim to phone_number.php
header( "refresh:3;url=phone_number.php" );
phone_number.php
- collects phone number in a form and posts to action2.php
<form action="action2.php" method="post">
action2.php
- second exfil email sent to same drop account in to.php
- then victim redirected to success.php
header("location: success.php");
success.php
- sends user to a legit pdf
header( "refresh:1;url=http://www.businessmodelcommunity.com/fs/Root/8jig8-businessmodelsbusinessstrategy.pdf" );




Comments
Post a Comment